Introduction
Today, I completed the Meow machine on Hack The Box (HTB). This is one of the easiest machines in HTB’s Starting Point, designed to introduce beginners to basic enumeration, port scanning, and service exploitation. Despite its simplicity, it highlights the dangers of weak credentials and misconfigurations in cybersecurity.
If you’re new to ethical hacking or penetration testing, this guide will walk you through the steps to exploit the Meow machine and capture the flag. 🚀
1. Setting Up the Environment
Before starting, ensure your setup is ready: ✅ Connected to HTB’s VPN using Pwnbox or OpenVPN
✅ Spawned the Meow machine and noted its IP address
For me, the target IP was 10.X.X.X, but yours may differ.
To verify connectivity, I ran:
ping 10.X.X.XA successful reply confirmed that I was ready to proceed.
2. Enumeration with Nmap
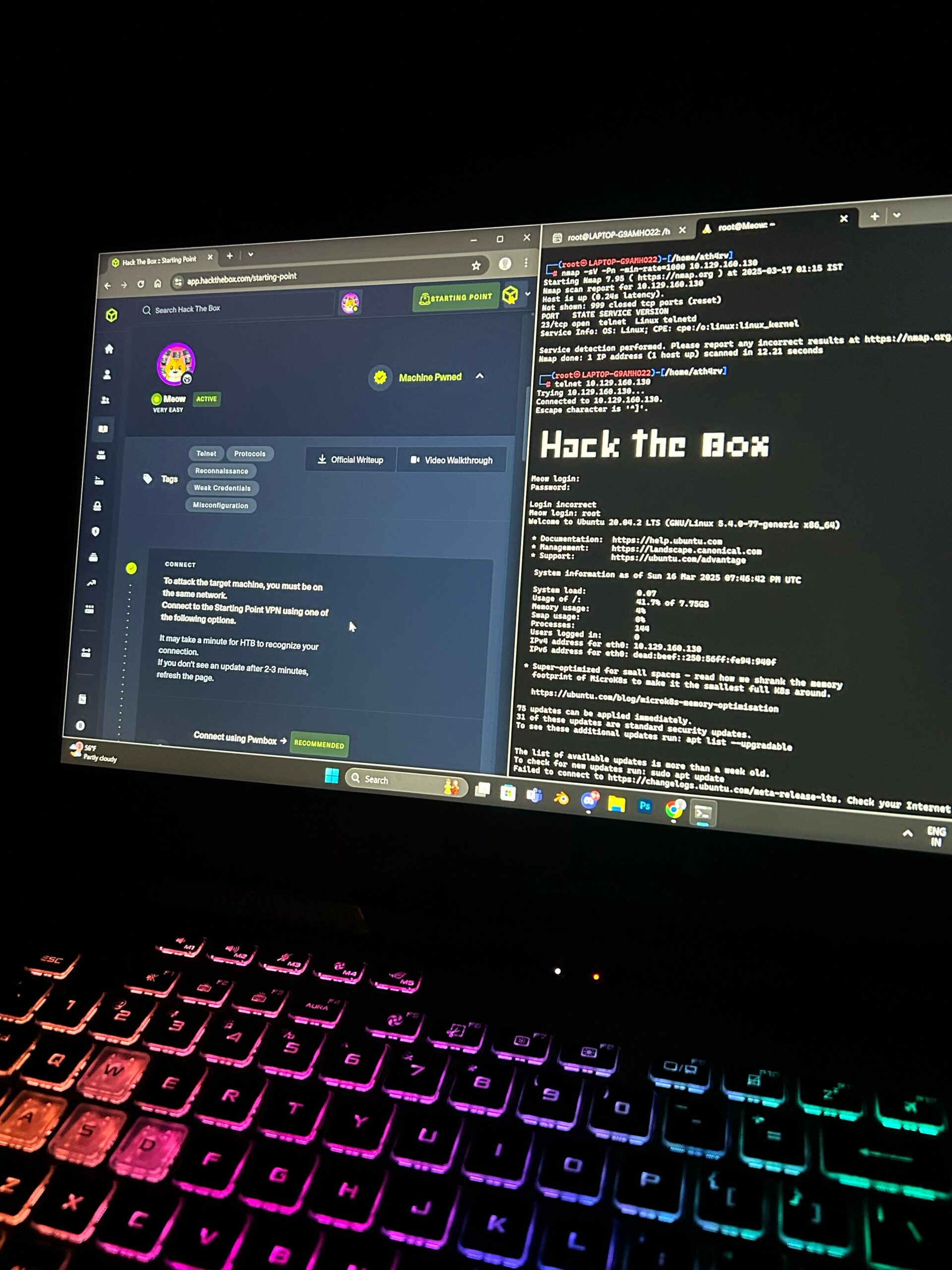
In penetration testing, enumeration is the first step. I used Nmap to scan for open ports and running services:
nmap -sV -Pn -T4 10.X.X.XScan Results:
Only one open port was found:
23/tcp open telnetThis meant that the Telnet service was active on the target machine.
3. Exploiting Telnet (Foothold)
Telnet is an outdated protocol for remote administration, notorious for transmitting data in plain text, making it highly insecure.
To connect, I used:
telnet 10.X.X.XIt prompted for login credentials. Since Telnet is often misconfigured, I tested default usernames: ✅ admin → ❌
✅ administrator → ❌
✅ root → ✅ (Success! No password required!)
This reveals a major security misconfiguration—allowing default root login without a password is a serious vulnerability.
4. Capturing the Flag (Privilege Escalation)
Once inside, I checked the home directory:
lsI found a file named flag.txt. To view its contents, I used:
cat flag.txtThis displayed the HTB flag, which I copied and submitted to complete the challenge. 🎉
Key Takeaways & Cybersecurity Best Practices
🔴 Disable Telnet – It’s outdated and insecure. Use SSH instead.
🔴 Default credentials are a major risk – Attackers often try common usernames and passwords first.
🔴 Enumeration is key – Even in simple machines, identifying open ports and services is crucial.
🔴 Hack The Box is a great learning platform – If you’re new to cybersecurity, start with Starting Point machines like Meow.
Final Thoughts
Although Meow is an easy box, it teaches essential penetration testing fundamentals. If you’re new to ethical hacking, I highly recommend starting here before moving on to tougher machines.
🔥 More walkthroughs and cybersecurity blogs coming soon—stay tuned! 🚀
Leave a Reply